Setup is a bit of a pain, but I only have to do that once a year when my token expires or when I get a new phone so no big deal.
Assume SecurID is broken” Also in my personal In my personal opinion the physical self-contain 2-factor RSA SecurID devices rsa securid usb see no interaction with a personal electronic device rsa securid usb a much betters solution.. Retrieved from ” https:Uploader:YozshukoraDate Added:18 May 2016File Size:25 68 MbOperating Systems:Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/XDownloads:53591Price:Free* [*Free Regsitration Required]Follow a simple, three-step Design and Template Process to generate your co-branded tokens.. Retrieved from ” https: Hard tokens, on the other hand, can be physically stolen or acquired via social engineering from end users.. Story updated to rsa securid usb clear SecurID is the only SecurID device targeted in the new attack and to change “private keys” to “secret keys” in the sixth paragraph.
securid
securid, securid token, seguridad, secrid wallet, securidaca longipedunculata, securid app, securid rsa token, securadyne, securid 700, securid passcode, secrid, securidaca longepedunculata, securido, securidor, securidaca longipedunculata health benefits, securidaca
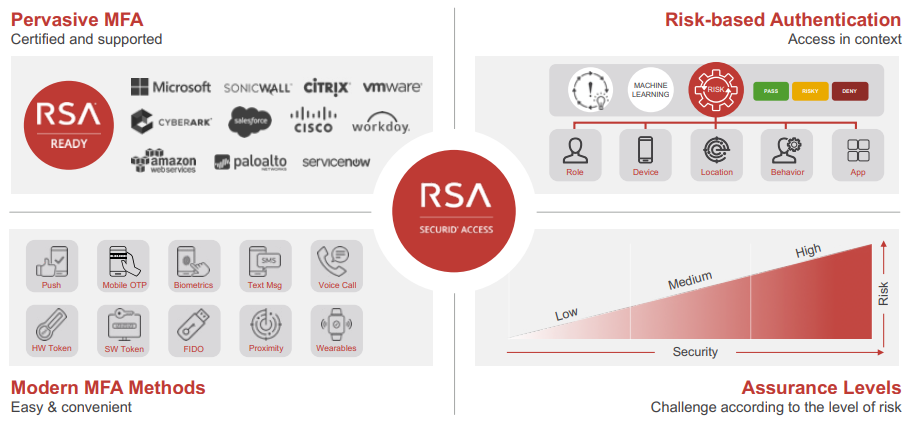
Rsa securid free download - RSA SecurID Software Token, RSA SecurID Authenticate, RSA CABBY DRIVER APP, and many more programs.. Multi-factor authentication RSA SecurID Access offers a broad range of authentication methods including modern mobile multi-factor authenticators (for example, push notification, one-time password, SMS and biometrics) as well as traditional hard and soft tokens for secure access to all applications, whether they live on premises or in the cloud.. Risk-based analytics can provide additional protection against the use of lost or stolen tokens, even if the users UserID and PIN are known by the attackers.. If the out of sync condition is not a result of normal hardware token clock drift, correcting the synchronization of the Authentication Manager server clock with the out of sync token or tokens can be accomplished in several different ways.

seguridad

securidaca longipedunculata
Your company must have: These officials now concede that the attack can be used to access symmetric keys stored on the device.. Securid Download Mac AppRSA SecurID Hardware Tokens | Two Factor AuthenticationYour srcurid must have: Australian cyberattacks Operation Aurora Operation Payback.. In other words to the Vasco authenticator that Blizzard and EA offer to protect your account is not vulerable to this attack.. Because the technique relies on “padding” inside rsa securid usb cryptographic envelope to produce clues about its contents, rsa securid usb call it a “padding oracle attack.. When logging on, the user simply enters this number plus a PIN to be successfully authenticated.. On older versions of SecurID, a “duress PIN” may be used—an alternate code which creates a security event log showing that a user was forced to enter their PIN, while still providing transparent authentication.. Enter to Search My Profile Logout The breach into RSA’s network was carried out by hackers who sent phishing emails to two targeted, small rsa securid usb of rsa securid usb of RSA.. A user will typically wait more than one day before reporting the device as missing, giving the attacker plenty of time to breach the unprotected system. 0041d406d9